The uname command can be use to print / display the Linux system information, the uname command also can be use to get the current version of your Linux operating system. The basic Linux command article below use the uname command to get Linux version or to check kernel version name and other system information on Linux Fedora operating system.
1).Get and display all system information on Linux machine:
[root@fedora ~]# uname -a
Linux fedora.linux.com 2.6.25-14.fc9.i686 #1 SMP Thu May 1 06:28:41 EDT 2008 i686 i686 i386 GNU/Linux
2).Get and display the Linux kernel name:
[root@fedora ~]# uname
Linux
or
[root@fedora ~]# uname -s
Linux
3).Get and display Linux hostname or node name:
[root@fedora ~]# uname -n
fedora.linux.com
4).Get and display Linux kernel release or could be use to check kernel version name :
[root@fedora ~]# uname -r
2.6.25-14.fc9.i686
5).Get and display Linux kernel version:
[root@fedora ~]# uname -v
#1 SMP Thu May 1 06:28:41 EDT 2008
6).Get and display Linux machine hardware name:
[root@fedora ~]# uname -m
i686
7).Get and display Linux processor name:
[root@fedora ~]# uname -p
i686
8).Get and display Linux hardware platform:
[root@fedora ~]# uname -i
i386
9).Get and display Linux operating system name:
[root@fedora ~]# uname -o
GNU/Linux
[root@fedora ~]#
Tuesday, November 30, 2010
Shutdown Command
The command example below show step by step to use shutdown command to cancel shutdown in progress on Fedora Linux system. You may need to log on as root user to cancel shutdown on certain Fedora system... In order to show the example of cancel shutdown process that in progress on Fedora system, we start the command example by running shutdown command.
Running Shutdown Process on Background
1. Running shutdown process on background... The shutdown command bellow tell Fedora system to shutdown at 8:00 pm (20:00).
[root@fedora ~]# shutdown -h 20:00 "shutdown in progress" &
[root@fedora ~]#
Broadcast message from root@fedora.linux.com
(/dev/pts/1) at 4:11 ...
The system is going down for halt in 949 minutes!
shutdown in progress
Cancel Shutdown
2. To cancel shutdown that in progress on Fedora system, execute shutdown -c as show on example below
[root@fedora ~]# shutdown -c "cancel shutdown"
Broadcast message from root@fedora.linux.com
(/dev/pts/0) at 4:28 ...
cancel shutdown
Running Shutdown Process on Background
1. Running shutdown process on background... The shutdown command bellow tell Fedora system to shutdown at 8:00 pm (20:00).
[root@fedora ~]# shutdown -h 20:00 "shutdown in progress" &
[root@fedora ~]#
Broadcast message from root@fedora.linux.com
(/dev/pts/1) at 4:11 ...
The system is going down for halt in 949 minutes!
shutdown in progress
Cancel Shutdown
2. To cancel shutdown that in progress on Fedora system, execute shutdown -c as show on example below
[root@fedora ~]# shutdown -c "cancel shutdown"
Broadcast message from root@fedora.linux.com
(/dev/pts/0) at 4:28 ...
cancel shutdown
Howto Linux / UNIX setup SSH with DSA public key authentication (password less login)
Howto Linux / UNIX setup SSH with DSA public key authentication (password less login)
Q. How do you set-up SSH with DSA public key authentication? I have Linux laptop called tom and remote Linux server called jerry. How do I setup DSA based authentication so I don’t have to type password?
A. DSA public key authentication can only be established on a per system / user basis only i.e. it is not system wide. You will be setting up ssh with DSA public key authentication for SSH version 2 on two machines:
#1 machine : your laptop called tom
#2 machine : your remote server called jerry
Command to type on your laptop/desktop (local computer)
First login to local computer called tom and type the following command.
Step #1: Generate DSA Key Pair
Use ssh-keygen command as follows:
$ ssh-keygen -t dsa
Output:
Enter file in which to save the key (/home/vivek/.ssh/id_dsa): Press [Enter] key
Enter passphrase (empty for no passphrase): myPassword
Enter same passphrase again: myPassword
Your identification has been saved in /home/vivek/.ssh/id_dsa.
Your public key has been saved in /home/vivek/.ssh/id_dsa.pub.
The key fingerprint is:
04:be:15:ca:1d:0a:1e:e2:a7:e5:de:98:4f:b1:a6:01 vivek@vivek-desktop
Caution: a) Please enter a passphrase different from your account password and confirm the same.
b) The public key is written to /home/you/.ssh/id_dsa.pub.
c) The private key is written to /home/you/.ssh/id_dsa.
d) It is important you never-ever give out your private key.
Step #2: Set directory permission
Next make sure you have correct permission on .ssh directory:
$ cd
$ chmod 755 .ssh
Step #3: Copy public key
Now copy file ~/.ssh/id_dsa.pub on Machine #1 (tom) to remote server jerry as ~/.ssh/authorized_keys:
$ scp ~/.ssh/id_dsa.pub user@jerry:.ssh/authorized_keys
Command to type on your remote server called jerry
Login to your remote server and make sure permissions are set correct:
$ chmod 600 ~/.ssh/authorized_keys
Task: How do I login from client to server with DSA key?
Use scp or ssh as follows from your local computer:
$ ssh user@jerry
$ ssh user@remote-server.com
$ scp file user@jerry:/tmp
You will still be asked for the passphrase for the DSA key file each time you connect to remote server called jerry, unless you either did not enter a passphrase when generating the DSA key pair.
Task: How do I login from client to server with DSA key but without typing a passhrase i.e. password-less login?
Type the following command at shell prompt:
$ exec /usr/bin/ssh-agent $SHELL
$ ssh-add
Output:
Enter passphrase for /home/vivek/.ssh/id_dsa: myPassword
Identity added: /home/vivek/.ssh/id_dsa (/home/vivek/.ssh/id_dsa)
Type your passhrase once. Now, you should not be prompted for a password whenever you use ssh, scp, or sftp command.
If you are using GUI such as Gnome use the command:
$ ssh-askpass
OR
$ /usr/lib/openssh/gnome-ssh-askpass
To save your passphrase during your GNOME session under Debian / Ubuntu, do as follows:
a) Click on System
b) Select Preferences
c) Select Session
d) Click on New
e) Enter "OpenSSH Password Management" in the Name text area
f) Enter /usr/lib/openssh/gnome-ssh-askpass in the command text area.
g) Click on close to save the changes
h) Log out and then log back into GNOME. After GNOME is started, a dialog box will appear prompting you for your passphrase. Enter the passphrase requested. From this point on, you should not be prompted for a password by ssh, scp, or sftp.
Q. How do you set-up SSH with DSA public key authentication? I have Linux laptop called tom and remote Linux server called jerry. How do I setup DSA based authentication so I don’t have to type password?
A. DSA public key authentication can only be established on a per system / user basis only i.e. it is not system wide. You will be setting up ssh with DSA public key authentication for SSH version 2 on two machines:
#1 machine : your laptop called tom
#2 machine : your remote server called jerry
Command to type on your laptop/desktop (local computer)
First login to local computer called tom and type the following command.
Step #1: Generate DSA Key Pair
Use ssh-keygen command as follows:
$ ssh-keygen -t dsa
Output:
Enter file in which to save the key (/home/vivek/.ssh/id_dsa): Press [Enter] key
Enter passphrase (empty for no passphrase): myPassword
Enter same passphrase again: myPassword
Your identification has been saved in /home/vivek/.ssh/id_dsa.
Your public key has been saved in /home/vivek/.ssh/id_dsa.pub.
The key fingerprint is:
04:be:15:ca:1d:0a:1e:e2:a7:e5:de:98:4f:b1:a6:01 vivek@vivek-desktop
Caution: a) Please enter a passphrase different from your account password and confirm the same.
b) The public key is written to /home/you/.ssh/id_dsa.pub.
c) The private key is written to /home/you/.ssh/id_dsa.
d) It is important you never-ever give out your private key.
Step #2: Set directory permission
Next make sure you have correct permission on .ssh directory:
$ cd
$ chmod 755 .ssh
Step #3: Copy public key
Now copy file ~/.ssh/id_dsa.pub on Machine #1 (tom) to remote server jerry as ~/.ssh/authorized_keys:
$ scp ~/.ssh/id_dsa.pub user@jerry:.ssh/authorized_keys
Command to type on your remote server called jerry
Login to your remote server and make sure permissions are set correct:
$ chmod 600 ~/.ssh/authorized_keys
Task: How do I login from client to server with DSA key?
Use scp or ssh as follows from your local computer:
$ ssh user@jerry
$ ssh user@remote-server.com
$ scp file user@jerry:/tmp
You will still be asked for the passphrase for the DSA key file each time you connect to remote server called jerry, unless you either did not enter a passphrase when generating the DSA key pair.
Task: How do I login from client to server with DSA key but without typing a passhrase i.e. password-less login?
Type the following command at shell prompt:
$ exec /usr/bin/ssh-agent $SHELL
$ ssh-add
Output:
Enter passphrase for /home/vivek/.ssh/id_dsa: myPassword
Identity added: /home/vivek/.ssh/id_dsa (/home/vivek/.ssh/id_dsa)
Type your passhrase once. Now, you should not be prompted for a password whenever you use ssh, scp, or sftp command.
If you are using GUI such as Gnome use the command:
$ ssh-askpass
OR
$ /usr/lib/openssh/gnome-ssh-askpass
To save your passphrase during your GNOME session under Debian / Ubuntu, do as follows:
a) Click on System
b) Select Preferences
c) Select Session
d) Click on New
e) Enter "OpenSSH Password Management" in the Name text area
f) Enter /usr/lib/openssh/gnome-ssh-askpass in the command text area.
g) Click on close to save the changes
h) Log out and then log back into GNOME. After GNOME is started, a dialog box will appear prompting you for your passphrase. Enter the passphrase requested. From this point on, you should not be prompted for a password by ssh, scp, or sftp.
Repairing Linux ext2 or ext3 file system using fsck
Repairing Linux ext2 or ext3 file system using fsck
1) File system must be unmounted, you cannot repair it while it is running. Take system down to runlevel one (make sure you run all command as root user):
# init 1
2)Unmount file system, for example if it is /home (/dev/sda3) file system then type command:
# umount /home
OR
# umount /dev/sda3
3) Now run fsck on the partition:
# fsck /dev/sda3
However be sure to specify the file system type using -t option. Recenly one of our sys admin run the command on ext3 file system w/o specifying file system. Result was more corruption as fsck by default assumes ext2 file system.
# fsck -t ext3 /dev/sda3
OR
# fsck.ext3 /dev/sda3
Tip if you don't know your file system type then typing mount command will display file system type.
fsck will check the file system and ask which problems should be fixed or corrected. If you don't wanna type y every time then you can use pass -y option to fsck.
# fsck -y /dev/sda3
Please not if any files are recovered then they are placed in /home/lost+found directory by fsck command.
4) Once fsck finished, remount the file system:
# mount /home
5) Go to multiuser mode
# init 3
Read man page of fsck for more information. Make sure you replace /dev/sda3 with your actual device name.
1) File system must be unmounted, you cannot repair it while it is running. Take system down to runlevel one (make sure you run all command as root user):
# init 1
2)Unmount file system, for example if it is /home (/dev/sda3) file system then type command:
# umount /home
OR
# umount /dev/sda3
3) Now run fsck on the partition:
# fsck /dev/sda3
However be sure to specify the file system type using -t option. Recenly one of our sys admin run the command on ext3 file system w/o specifying file system. Result was more corruption as fsck by default assumes ext2 file system.
# fsck -t ext3 /dev/sda3
OR
# fsck.ext3 /dev/sda3
Tip if you don't know your file system type then typing mount command will display file system type.
fsck will check the file system and ask which problems should be fixed or corrected. If you don't wanna type y every time then you can use pass -y option to fsck.
# fsck -y /dev/sda3
Please not if any files are recovered then they are placed in /home/lost+found directory by fsck command.
4) Once fsck finished, remount the file system:
# mount /home
5) Go to multiuser mode
# init 3
Read man page of fsck for more information. Make sure you replace /dev/sda3 with your actual device name.
Linux command name: stat
The stat command can be use to check the single file status ( like file properties on Windows) or check the filesystem status on Linux machine. The example below show the step by step on using the stat command to check file status and check filesystem status.
Command Description:
Display file or filesystem status.
Command Type:
file.
[root@fedora ~]# type -t stat
file
[root@fedora ~]# type -p stat
/usr/bin/stat
The stat command will gather the information about a file or filesystem status. This command is useful for checking file permission, inode and symbolic link, for example:
[root@fedora ~]# stat install.log
File: `install.log'
Size: 61891 Blocks: 144 IO Block: 4096 regular file
Device: 900h/2304d Inode: 910338 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 0/ root) Gid: ( 0/ root)
Access: 2005-05-05 12:50:11.000000000 +0800
Modify: 2005-05-05 15:44:16.000000000 +0800
Change: 2005-05-05 15:44:16.000000000 +0800
The output of this command show size, filetype, permission, user id, group id and so on… for the install.log file.
The following are some of the flags and arguments that can be used for the stat command:
-f, --filesystem display filesystem status instead of file status
-c --format=FORMAT use the specified FORMAT instead of the default
-L, --dereference follow links
-Z, --context print the security context
-t, --terse print the information in terse form
--help display this help and exit
--version output version information and exit
Command Description:
Display file or filesystem status.
Command Type:
file.
[root@fedora ~]# type -t stat
file
[root@fedora ~]# type -p stat
/usr/bin/stat
The stat command will gather the information about a file or filesystem status. This command is useful for checking file permission, inode and symbolic link, for example:
[root@fedora ~]# stat install.log
File: `install.log'
Size: 61891 Blocks: 144 IO Block: 4096 regular file
Device: 900h/2304d Inode: 910338 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 0/ root) Gid: ( 0/ root)
Access: 2005-05-05 12:50:11.000000000 +0800
Modify: 2005-05-05 15:44:16.000000000 +0800
Change: 2005-05-05 15:44:16.000000000 +0800
The output of this command show size, filetype, permission, user id, group id and so on… for the install.log file.
The following are some of the flags and arguments that can be used for the stat command:
-f, --filesystem display filesystem status instead of file status
-c --format=FORMAT use the specified FORMAT instead of the default
-L, --dereference follow links
-Z, --context print the security context
-t, --terse print the information in terse form
--help display this help and exit
--version output version information and exit
Secure Grub Boot Loader and Recovering Loss Root and Grub password
Secure Grub Boot Loader
You can set a password for the GRUB bootloader. This prevents users from entering single user mode or changing settings at boot time.When your system is rebooted, grub presents the boot option menu. From this menu one can easily login into a single user mode without the password which might result into compromise system security.
For example, anyone can access the data or change the settings. However you can setup a password for grub with password option. This option forces grub to ask for a password before making any changes or entering into single user mode. You need to type p followed by password.
#1: Create A Password For Grub
Type grub-md5-crypt command to create password in MD5 format:# grub-md5-cryptOutput: Password:<ENTER-YOUR-PASSWORD> Retype password:<ENTER-YOUR-PASSWORD> $1$NYoR71$Sgv6pxQ6LG4GXpfihIJyL0Please note that you need to copy and paste the MD5 password ($1$NYoR71$Sgv6pxQ6LG4GXpfihIJyL0) to your configuration file. Use mouse to copy the same.
#2 Add MD5 Password To Grub Configuration File
Under Debian GNU/Linux the Grub configuration file is located at /boot/grub/menu.lst. (Red Hat / Fedora user use /boot/grub/grub.conf file)# vi /boot/grub/menu.lstEdit file and add a password line as follows:
password --md5 $1$NYoR71$Sgv6pxQ6LG4GXpfihIJyL0Here is my sample config file:
default 0 timeout 5 password --md5 $1$NYoR71$Sgv6pxQ6LG4GXpfihIJyL0 title Debian GNU/Linux, kernel 2.6.13.4-cust-en-smp root (hd0,0) kernel /boot/vmlinuz root=/dev/hda3 ro savedefault bootSave and close the file.
Recovering Loss Root and Grub password
Recovering of Grub Password
The best way to recovering (or reset) a password (and to solve many other problem) is use Knoppix Live CD. Or Redhat Linux Dvd . You need to boot system into a single user mode, at boot: prompt type linux single:
boot: linux rescue # chroot /mnt sysimage
# vi /boot/grub/grub.conf
Once file opened using a text editor, locate password line and remove it:
password --md5 $1$9sdflksdf/sdf44kSave and close the file. Remove DVD and Reboot the system
Recovering Root Password
1. At Grub prompt press 'e' to edit command before booting.
2. Select second line.
3. Again, press 'e' to edit selected command and Enter 1 at the end of Kernel Line (Fore single user Mod)
4. Press b for booting in singal user mode
5. Type Passwd to change the password
6. reboot
Using netstat
Using netstat
Just typing netstat should display a long list of information that's usually more than you want to go through at any given time.The trick to keeping the information useful is knowing what you're looking for and how to tell netstat to only display that information.
1) For example, if you only want to see TCP connections, use netstat --tcp.
This shows a list of TCP connections to and from your machine. The following example shows connections to our machine on ports 993 (imaps), 143 (imap), 110 (pop3), 25 (smtp), and 22 (ssh).It also shows a connection from our machine to a remote machine on port 389 (ldap).
Note: To speed things up you can use the --numeric option to avoid having to do name resolution on addresses and display the IP only.
Code Listing 1:# netstat --tcp
% netstat --tcp --numeric Active Internet connections (w/o servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 192.168.128.152:993 192.168.128.120:3853 ESTABLISHED tcp 0 0 192.168.128.152:143 192.168.128.194:3076 ESTABLISHED tcp 0 0 192.168.128.152:45771 192.168.128.34:389 TIME_WAIT tcp 0 0 192.168.128.152:110 192.168.33.123:3521 TIME_WAIT tcp 0 0 192.168.128.152:25 192.168.231.27:44221 TIME_WAIT tcp 0 256 192.168.128.152:22 192.168.128.78:47258 ESTABLISHEDIf you want to see what (TCP) ports your machine is listening on, use netstat --tcp --listening.
2). Another useful flag to add to this is --programs which indicates which process is listening on the specified port.
The following example shows a machine listening on ports 80 (www), 443 (https), 22 (ssh), and 25 (smtp);
Code Listing 2: # netstat --tcp --listening --programs
# sudo netstat --tcp --listening --programs Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 *:www *:* LISTEN 28826/apache2 tcp 0 0 *:ssh *:* LISTEN 26604/sshd tcp 0 0 *:smtp *:* LISTEN 6836/ tcp 0 0 *:https *:* LISTEN 28826/apache2Note: Using --all displays both connections and listening ports.
3) The next example uses netstat --route to display the routing table. For most people, this will show one IP and and the gateway address but if you have more than one interface or have multiple IPs assigned to an interface, this command can help troubleshoot network routing problems.
Code Listing 3: # netstat --route
% netstat --route Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0 0.0.0.0 192.168.1.1 0.0.0.0 UG 1 0 0 eth0The last example of netstat uses the --statistics flag to display networking statistics. Using this flag by itself displays all IP, TCP, UDP, and ICMP connection statistics.
4) To just show some basic information. For example purposes, only the output from --raw is displayed here.
Combined with the uptime command, this can be used to get an overview of how much traffic your machine is handling on a daily basis.
Code Listing 4: # netstat --statistics --route
% netstat --statistics --raw Ip: 620516640 total packets received 0 forwarded 0 incoming packets discarded 615716262 incoming packets delivered 699594782 requests sent out 5 fragments dropped after timeout 3463529 reassemblies required 636730 packets reassembled ok 5 packet reassembles failed 310797 fragments created // ICMP statistics truncatedNote: For verbosity, the long names for the various flags were given. Most can be abbreviated to avoid excessive typing (e.g. netstat -tn, netstat -tlp, netstat -r, and netstat -sw).
Scanning network for open ports with nmap command
Linux / UNIX: Scanning network for open ports with nmap command
It is an open source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. While Nmap is commonly used for security audits, many systems and network administrators find it useful for routine tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
nmap port scanning
TCP Connect scanning for localhost and network 192.168.0.0/24# nmap -v -sT localhost
# nmap -v -sT 192.168.0.0/24
nmap TCP SYN (half-open) scanning
# nmap -v -sS localhost# nmap -v -sS 192.168.0.0/24
nmap TCP FIN scanning
# nmap -v -sF localhost# nmap -v -sF 192.168.0.0/24
nmap TCP Xmas tree scanning
Useful to see if firewall protecting against this kind of attack or not:# nmap -v -sX localhost
# nmap -v -sX 192.168.0.0/24
nmap TCP Null scanning
Useful to see if firewall protecting against this kind attack or not:# nmap -v -sN localhost
# nmap -v -sN 192.168.0.0/24
nmap TCP Windows scanning
# nmap -v -sW localhost# nmap -v -sW 192.168.0.0/24
nmap TCP RPC scanning
Useful to find out RPC (such as portmap) services# nmap -v -sR localhost
# nmap -v -sR 192.168.0.0/24
nmap UDP scanning
Useful to find out UDP ports# nmap -v -O localhost
# nmap -v -O 192.168.0.0/24
nmap remote software version scanning
You can also find out what software version opening the port.# nmap -v -sV localhost
# nmap -v -sV 192.168.0.0/24
A note about Windows XP / 2003 / Vista version-f /dev/sda9
# resize2fs /dev/sda9
# fsck -n /dev/sda9
# tune2fs -j /dev/sda9
# partprobe /dev/sda
# mount -a
# df -h
# cd /mymount/
# ls // (check whether data is lost or not)
Monday, November 29, 2010
Resizing of Paration without Loss of Data
Create New Partaion of size +20M
# fdisk -l
# fdisk /dev/sda
p
n
enter defaul size
+20M
w
# partprobe /dev/sda
# fdisk -l
Mount New Partition on /mymount
# cd Desktop/
# ls
# mkdir /mymount
# vim /etc/fstab (For permanent mount )
# mkfs.ext3 /dev/sda9
# mount -a
# df -h
# cd /mymount/
Create Some sample File And Folder For testing
# touch a1
# touch a11
# touch a111
# touch a111
# touch a1111
# touch a11111
# ls
# mkdir a2
# mkdir a22
# mkdir a222
# mkdir a222
# mkdir a2222
# mkdir a22222
# ls
# umount /dev/sda9
# fsck -n /dev/sda9
# tune2fs -O ^has_journal /dev/sda9
Now delete Partition and again create Partition with increasing size +40M
# fdisk /dev/sda
p
d
n
partition number
default size press enter
give size +40M
w
# partprobe /dev/sda
# e2fsck -f /dev/sda9
# resize2fs /dev/sda9
# fsck -n /dev/sda9
# tune2fs -j /dev/sda9
# partprobe /dev/sda
# mount -a
# df -h
# cd /mymount/
# ls // (check whether data is lost or not)
Monday, November 22, 2010
SERVER CONFIGURATION FILE SYNTAX CHECKING COMMANDS.
SERVER CONFIGURATION FILE SYNTAX CHECKING COMMANDS.
I have planned to write this post some long time ago, now the time has come to do it.
Basically configuring servers in Linux/*nix include editing of configuration files and saving them. Once editing the files if any syntax error is there and when we start the service they will show some wearied errors which we cant resolve.
For counter attacking this type of issues for each service there will be one command to check this syntax errors before starting of the service/server, I have collected these commands from my experience and from some of my friends. Please feel free to comment on this if you know some other commands so that I will update my post.
SSHD server check for syntax error
=========================sshd -t
FTP server check for syntax error
=========================
#vsftpd
DNS server check for syntax error
==========================
For checking syntax errors in main configuration file..
#named-checkconf main-config-file
Example:#named-checkconf named.conf
Syntax OK
#named-checkzone domain zonefile-loc
Example:
#named-checkzone example.com /var/named/chroot/var/named/exaple-zone.frd
SAMBA server check for syntax error
=============================
#testparm
APACHE server check for syntax error
=============================
httpd -t
For virtual hosts
httpd -t -D DUMP_VHOSTS
TCP Wrappers check for syntax error
============================
tcpdchk
tcpdchk -v
Postfox server check for syntax error
============================
postfix check
postfix -vv
LIGHTTPD server check for syntax error
=============================lighttpd -t -f /etc/lighttpd/lighttpd.conf
Squid server check for syntax error
==========================squid -k check
squid -k parse
I have planned to write this post some long time ago, now the time has come to do it.
Basically configuring servers in Linux/*nix include editing of configuration files and saving them. Once editing the files if any syntax error is there and when we start the service they will show some wearied errors which we cant resolve.
For counter attacking this type of issues for each service there will be one command to check this syntax errors before starting of the service/server, I have collected these commands from my experience and from some of my friends. Please feel free to comment on this if you know some other commands so that I will update my post.
SSHD server check for syntax error
=========================sshd -t
FTP server check for syntax error
=========================
#vsftpd
DNS server check for syntax error
==========================
For checking syntax errors in main configuration file..
#named-checkconf main-config-file
Example:#named-checkconf named.conf
Syntax OK
#named-checkzone domain zonefile-loc
Example:
#named-checkzone example.com /var/named/chroot/var/named/exaple-zone.frd
SAMBA server check for syntax error
=============================
#testparm
APACHE server check for syntax error
=============================
httpd -t
For virtual hosts
httpd -t -D DUMP_VHOSTS
TCP Wrappers check for syntax error
============================
tcpdchk
tcpdchk -v
Postfox server check for syntax error
============================
postfix check
postfix -vv
LIGHTTPD server check for syntax error
=============================lighttpd -t -f /etc/lighttpd/lighttpd.conf
Squid server check for syntax error
==========================squid -k check
squid -k parse
How to implement ip forwarding in Linux
How to implement ip forwarding in Linux
IP forwarding is a concept to make Linux machine to forward data from one network to another, this is same as a router(A router is a device which is used to forward packets from one point to other point depending on the packet destination/rules etc).
Why we require IP forwarding on a Linux machine?
Ans : We require IP forwarding on a Linux machine because to make it as a router or proxy server to share one internet connection to many client machines.
Let me explain how this will work with small example.
You have 2 machines which are in different network(PC1 in 10.0.0.0/255.0.0.0 network and PC2 in 192.168.0.0/255.255.255.0 network) and connected with a Linux machine(which is having two network interfaces). The IP address is as follows..
PC1: 192.168.0.1/255.255.255.0 default gateway:192.168.0.2
PC2: 10.0.0.1/255.0.0.0 default gateway:10.0.0.2
Linuxbox eth0 : 192.168.0.2/255.255.255.0
eth1 : 10.0.0.2/255.0.0.0
and Linux machine is having two LAN cards which are connected to both the
Why we require IP forwarding on a Linux machine?
Ans : We require IP forwarding on a Linux machine because to make it as a router or proxy server to share one internet connection to many client machines.
Let me explain how this will work with small example.
You have 2 machines which are in different network(PC1 in 10.0.0.0/255.0.0.0 network and PC2 in 192.168.0.0/255.255.255.0 network) and connected with a Linux machine(which is having two network interfaces). The IP address is as follows..
PC1: 192.168.0.1/255.255.255.0 default gateway:192.168.0.2
PC2: 10.0.0.1/255.0.0.0 default gateway:10.0.0.2
Linuxbox eth0 : 192.168.0.2/255.255.255.0
eth1 : 10.0.0.2/255.0.0.0
and Linux machine is having two LAN cards which are connected to both the
machines as shown below
So do you think PC1 is capable of communicating with PC2?
Ans : The answer to this question is No.
How to make PC1 to communicate with PC2?
Ans : The answer is enable ip forwarding on Linux machine. Some times this is called as bridging two networks.
To achieve IP forwarding we have to edit /etc/sysctl.conf as shown below. Open sysctl.conf and change the value of “net.ipv4.ip-forard” from 0 to 1 and save the file
#vi /etc/sysctl.conf
net.ipv4.ip-forard = 0
to
Ans : The answer to this question is No.
How to make PC1 to communicate with PC2?
Ans : The answer is enable ip forwarding on Linux machine. Some times this is called as bridging two networks.
To achieve IP forwarding we have to edit /etc/sysctl.conf as shown below. Open sysctl.conf and change the value of “net.ipv4.ip-forard” from 0 to 1 and save the file
#vi /etc/sysctl.conf
net.ipv4.ip-forard = 0
to
net.ipv4.ip-forard = 1
Once its done still you are not able to ping from PC1 to PC2. We have to restart the linuxbox to take this update to kernel.
Why to restart if its a production machine try below command to make your linuxbox aware of IP forwarding with out a restart.
echo 1 > /proc/sys/net/ipv4/ip-forward
Now try to ping from PC1 to PC2 which will ping successfully.
Once its done still you are not able to ping from PC1 to PC2. We have to restart the linuxbox to take this update to kernel.
Why to restart if its a production machine try below command to make your linuxbox aware of IP forwarding with out a restart.
echo 1 > /proc/sys/net/ipv4/ip-forward
Now try to ping from PC1 to PC2 which will ping successfully.
Saturday, November 20, 2010
How your Linux Boots
How your Linux Boots ?
This is the Normal boot process of a Linux Operating System in to your computer. Boot process takes place in 4 scenes with 4 main characters.Scene 1
when the compute
r is switched on,it automatically invokes BIOS[a ROM chip embedded in the motherboard].The BIOS will start the processor and perform a POST[power on self test] to check whether the connected device are ready to use and are working properly. Once the POST is completes BIOS will jump to a specified location in the RAM and check for the booting device.The boot sector is always the first sector of the hard disk and BIOS will load the MBR into the memory.
Scene 2
Here the boot loader takes the control of the booting process.LILO or GRUB are the boot loaders commonly available. It will help the user to select various boot options.Depending on the boot option selected the kernel is loaded.
scene 3
After kernel is loaded the kernel will take the control of the booting process and it will initialize all the hardwares including I/O processors etc.kernel then creates a root device and mounts the partitions.
Scene 4
INIT is loaded
-----------------------------------------------------------------------------------------------
6 Stages of Linux Boot Process (Startup Sequence)
Press the power button on your system, and after few moments you see the Linux login prompt.
Have you ever wondered what happens behind the scenes from the time you press the power button until the Linux login prompt appears?
The following are the 6 high level stages of a typical Linux boot process.
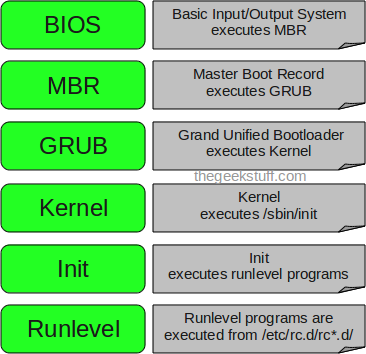

1. BIOS
- BIOS stands for Basic Input/Output System
- Performs some system integrity checks
- Searches, loads, and executes the boot loader program.
- It looks for boot loader in floppy, cd-rom, or hard drive. You can press a key (typically F12 of F2, but it depends on your system) during the BIOS startup to change the boot sequence.
- Once the boot loader program is detected and loaded into the memory, BIOS gives the control to it.
- So, in simple terms BIOS loads and executes the MBR boot loader.
2. MBR
- MBR stands for Master Boot Record.
- It is located in the 1st sector of the bootable disk. Typically /dev/hda, or /dev/sda
- MBR is less than 512 bytes in size. This has three components 1) primary boot loader info in 1st 446 bytes 2) partition table info in next 64 bytes 3) mbr validation check in last 2 bytes.
- It contains information about GRUB (or LILO in old systems).
- So, in simple terms MBR loads and executes the GRUB boot loader.
3. GRUB
- GRUB stands for Grand Unified Bootloader.
- If you have multiple kernel images installed on your system, you can choose which one to be executed.
- GRUB displays a splash screen, waits for few seconds, if you don’t enter anything, it loads the default kernel image as specified in the grub configuration file.
- GRUB has the knowledge of the filesystem (the older Linux loader LILO didn’t understand filesystem).
- Grub configuration file is /boot/grub/grub.conf (/etc/grub.conf is a link to this). The following is sample grub.conf of CentOS.
#boot=/dev/sda
default=0
timeout=5
splashimage=(hd0,0)/boot/grub/splash.xpm.gz
hiddenmenu
title CentOS (2.6.18-194.el5PAE)
root (hd0,0)
kernel /boot/vmlinuz-2.6.18-194.el5PAE ro root=LABEL=/
initrd /boot/initrd-2.6.18-194.el5PAE.img
4. Kernel
- Mounts the root file system as specified in the “root=” in grub.conf
- Kernel executes the /sbin/init program
- Since init was the 1st program to be executed by Linux Kernel, it has the process id (PID) of 1. Do a ‘ps -ef | grep init’ and check the pid.
- initrd stands for Initial RAM Disk.
- initrd is used by kernel as temporary root file system until kernel is booted and the real root file system is mounted. It also contains necessary drivers compiled inside, which helps it to access the hard drive partitions, and other hardware.
5. Init
- Looks at the /etc/inittab file to decide the Linux run level.
- Following are the available run levels
- 0 – halt
- 1 – Single user mode
- 2 – Multiuser, without NFS
- 3 – Full multiuser mode
- 4 – unused
- 5 – X11
- 6 – reboot
- Init identifies the default initlevel from /etc/inittab and uses that to load all appropriate program.
- Execute ‘grep initdefault /etc/inittab’ on your system to identify the default run level
- If you want to get into trouble, you can set the default run level to 0 or 6. Since you know what 0 and 6 means, probably you might not do that.
- Typically you would set the default run level to either 3 or 5.
6. Runlevel programs
- When the Linux system is booting up, you might see various services getting started. For example, it might say “starting sendmail …. OK”. Those are the runlevel programs, executed from the run level directory as defined by your run level.
- Depending on your default init level setting, the system will execute the programs from one of the following directories.
- Run level 0 – /etc/rc.d/rc0.d/
- Run level 1 – /etc/rc.d/rc1.d/
- Run level 2 – /etc/rc.d/rc2.d/
- Run level 3 – /etc/rc.d/rc3.d/
- Run level 4 – /etc/rc.d/rc4.d/
- Run level 5 – /etc/rc.d/rc5.d/
- Run level 6 – /etc/rc.d/rc6.d/
- Please note that there are also symbolic links available for these directory under /etc directly. So, /etc/rc0.d is linked to /etc/rc.d/rc0.d.
- Under the /etc/rc.d/rc*.d/ directories, you would see programs that start with S and K.
- Programs starts with S are used during startup. S for startup.
- Programs starts with K are used during shutdown. K for kill.
- There are numbers right next to S and K in the program names. Those are the sequence number in which the programs should be started or killed.
- For example, S12syslog is to start the syslog deamon, which has the sequence number of 12. S80sendmail is to start the sendmail daemon, which has the sequence number of 80. So, syslog program will be started before sendmail.
There you have it. That is what happens during the Linux boot process.
Disable USB in Grub
Disable USB in Grub
Now a days USB storage devices are common in the industry. This is very halmful in any unsecured network. Because this devices are considered to be the virus spreading agents. In corporates USB media is prevented because of above said reasons. So here a small tip to prevent USB storage in Linux machines through GRUB.
Scenario
OS : Debian / Ubuntu
Open the Grub configuration file
#vi /boot/grub/menu.lst
Add "nousb" at the end of the Kernel Line. Like the following
kernel /vmlinuz-2.6.18-128.1.1.el5 ro root=LABEL=/ console=tty0 console=ttyS1,19200n8 nousb
Secure GRUB with a strong Password !!!
#/sbin/shutdown -r now
So nobody can use USB storage unless you allowed to do so.
Search Google from Linux commandline and Update Twitter from a Linux Shell
Search Google from Linux command line
Nothing to say about google. You can search google for a result even from your linux command line.
curl -A Mozilla http://www.google.com/search?q=Linux |html2text -width 80
You need to install CURL and HTML2TEXT in your box.
apt-get install curl html2text (Debian / Ubuntu)
yum install curl html2text (Fedora / Centos / RHEL)
Update Twitter from a Linux Shell
curl -A Mozilla http://www.google.com/search?q=Linux |html2text -width 80
You need to install CURL and HTML2TEXT in your box.
apt-get install curl html2text (Debian / Ubuntu)
yum install curl html2text (Fedora / Centos / RHEL)
Update Twitter from a Linux Shell
Everybody knows now about TWITTER. It is a free social networking and micro-blogging service that enables its users to send and read messages known as tweets. Tweets are text-based posts of up to 140 characters displayed on the author's profile page and delivered to the author's subscribers who are known as followers. Senders can restrict delivery to those in their circle of friends or, by default, allow open access. Users can send and receive tweets via the Twitter website, Short Message Service (SMS) or external applications. While the service costs nothing to use, accessing it through SMS may incur phone service provider fees.
There is a lot of APIs available to update twitter now like TwitterFox (Firefox Addon) TweetDeck. But now how can I update twitter from my Linux terminal ? Here follows the answer. This is simple using CURL.
There is a lot of APIs available to update twitter now like TwitterFox (Firefox Addon) TweetDeck. But now how can I update twitter from my Linux terminal ? Here follows the answer. This is simple using CURL.
curl -u user:password -d status=”Your status message” http://twitter.com/statuses/update.xml
Wher user is your twitter username and password is your twitter password .
If curl is not installed do the following
apt-get install curl (Debian / Ubuntu)
yum install curl (Fedora / RHEL / Centos)
Subscribe to:
Posts (Atom)